In an era of cloud migration, remote work, and sophisticated cyber threats, the traditional castle-and-moat approach to security has become obsolete. The new mantra echoing through corporate boardrooms and government agencies is "Never Trust, Always Verify." This philosophy, known as Zero Trust Security, is rapidly becoming the standard for modern digital defense, driving a massive shift in strategy and investment across the globe.
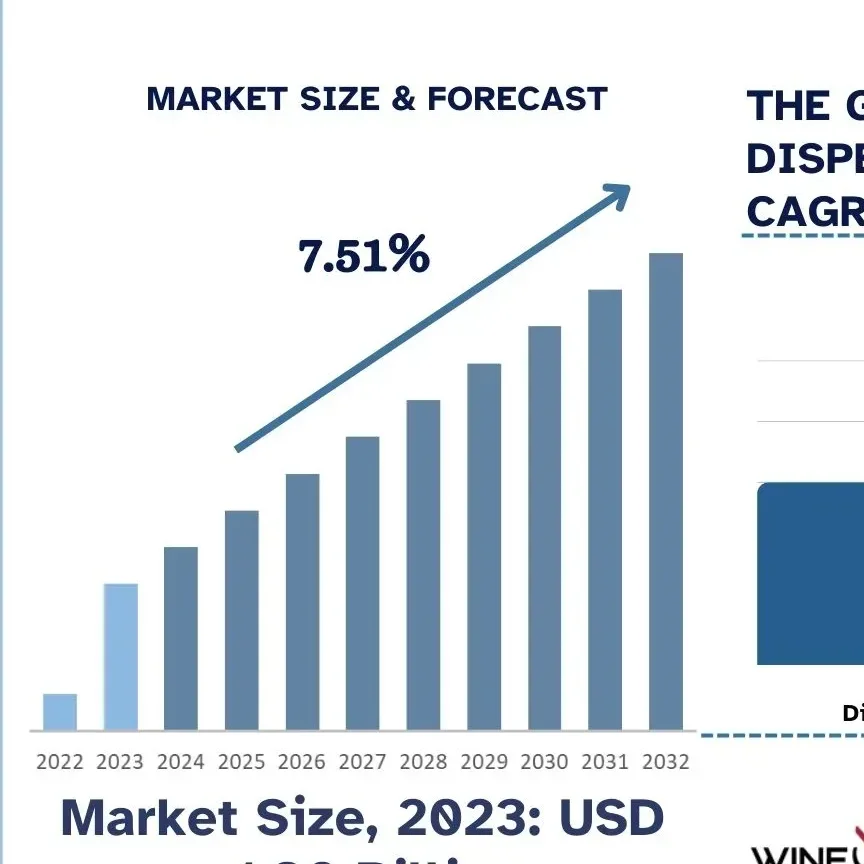
This strategic pivot is backed by significant financial commitment. According to Straits research, the global zero trust security market size was valued at USD 29.14 billion in 2024 and is expected to grow from USD 33.9 billion in 2025 to reach USD 113.6 billion by 2033, growing at a CAGR of 16.32% during the forecast period (2025-2033). This explosive growth reflects the urgency with which organizations are moving to adopt a model that assumes breach and verifies every request as though it originates from an untrusted network.
Key Players and Competitive Strategies: A Battle for Architectural Control
The Zero Trust landscape is a dynamic battleground where established security giants, cloud providers, and specialized innovators are vying for dominance.
-
Palo Alto Networks (USA): A leader in the space, Palo Alto has built a comprehensive Zero Trust ecosystem through its Prisma SASE (Secure Access Service Edge) platform. Their strategy involves integrating network security, cloud security, and security operations into a single, cloud-delivered offering. Recent updates include enhanced AI-driven policy recommendations to automate enforcement.
-
Zscaler (USA): A pure-play cloud security company, Zscaler’s entire business is built on a Zero Trust foundation. Its Zero Trust Exchange platform is a massive distributed cloud that acts as an intermediary for all user-to-application traffic, enforcing strict identity-centric policies. The company continues to expand its global footprint, adding more data centers to reduce latency worldwide.
-
Microsoft (USA): Leveraging its entrenched position in enterprise IT, Microsoft is aggressively pushing its Zero Trust suite built around Azure Active Directory for identity, Microsoft Defender for endpoint security, and Microsoft Entra for conditional access. Its unique advantage is the deep integration with the ubiquitous Windows and Microsoft 365 ecosystems.
-
CrowdStrike (USA): Coming from the endpoint security perspective, CrowdStrike’s Falcon platform positions the endpoint as a key control point for Zero Trust. Its recent acquisition of Humio enhances its threat-hunting capabilities, allowing it to correlate endpoint data with logs from across the IT environment for better policy enforcement.
-
Akamai Technologies (USA): Originally a content delivery network, Akamai has evolved into a significant SASE and Zero Trust player. Its acquisition of Guardicore bolstered its micro-segmentation capabilities, a critical component for protecting data centers and cloud workloads after perimeter defenses have been bypassed.
Emerging Trends: The Evolution of "Verify"
The implementation of Zero Trust is becoming more sophisticated, moving beyond basic concepts:
-
Identity-Centric Security: The core of Zero Trust is shifting from network IP addresses to user and device identity. Multi-factor authentication (MFA) is now considered table stakes, with trends moving towards continuous authentication based on user behavior analytics and biometrics.
-
Micro-segmentation: This technique involves creating secure zones within data centers and cloud environments to isolate workloads and protect them individually. Companies like Illumio (USA) specialize in this, preventing lateral movement by attackers who have breached the initial defenses.
-
Zero Trust Network Access (ZTNA): ZTNA is rapidly replacing legacy VPNs. It provides secure, granular access to specific applications rather than granting broad access to the entire network. This is a key offering from players like Zscaler and Palo Alto Networks.
-
Integration with AI and ML: Artificial intelligence is being used to analyze vast amounts of data to establish normal baselines for user and device behavior, enabling systems to automatically flag and block anomalous activity in real-time.
Recent News and Global Updates
-
United States: The White House's Executive Order 14028 has made Zero Trust adoption mandatory for all federal agencies, creating a massive wave of procurement and implementation projects. This has spurred innovation from all major players seeking government contracts.
-
Europe: The European Union Agency for Cybersecurity (ENISA) is actively promoting Zero Trust architectures as part of its cybersecurity strategy. Companies like Siemens (Germany) are developing Zero Trust frameworks tailored for operational technology (OT) and critical infrastructure.
-
Asia-Pacific: Countries like Japan and Australia are witnessing rapid adoption, driven by new data protection regulations and increasing cyber threats. Local service providers are partnering with global leaders to offer managed Zero Trust services to regional businesses.
Summary
The adoption of Zero Trust is no longer a speculative trend but a fundamental restructuring of cybersecurity.